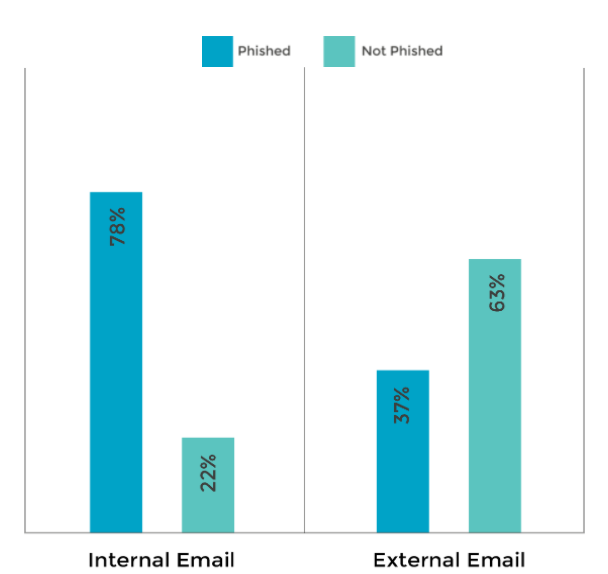
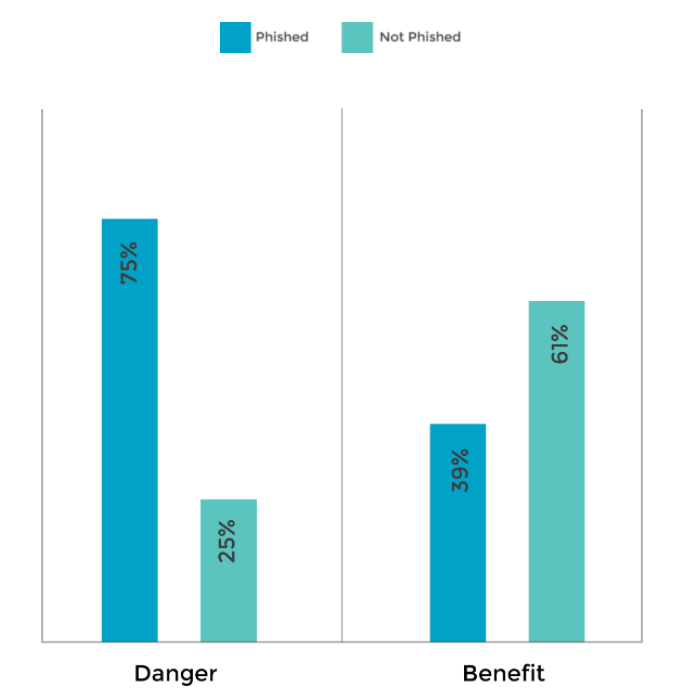
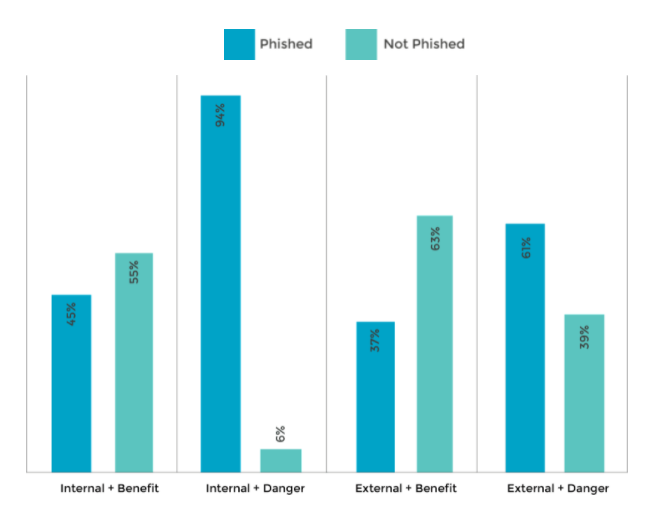
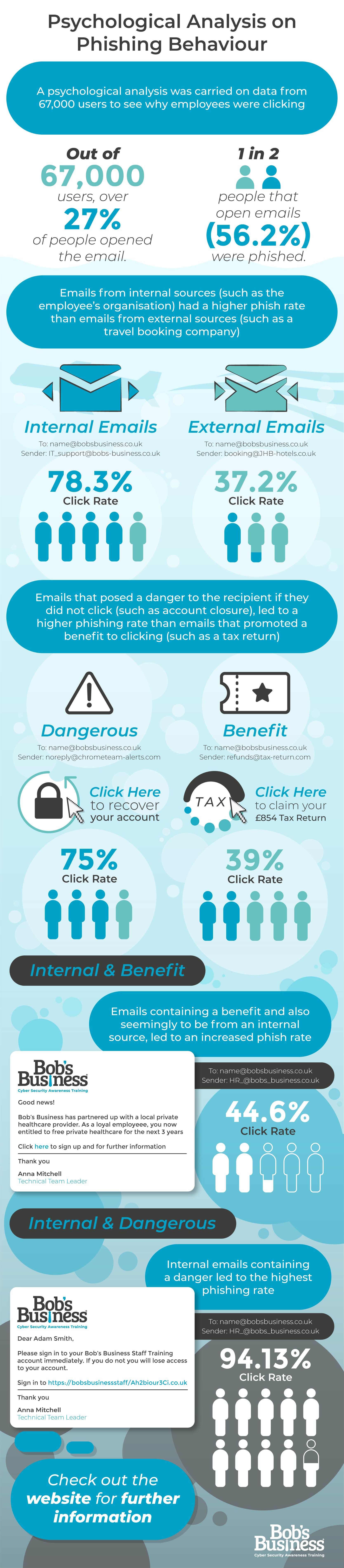
Let’s face it, GDPR legislation isn’t an easy read. Scrap that – it’s a slog. It’s so vast, in fact, that you can spend hours reading it and not understand very much at all.
The good news, however, is that it gets significantly easier once you understand what the jargon means and how it all links together.
To help out, we’ve put together this helpful GDPR jargon buster which you can use as a primer before undergoing GDPR training and diving into the intricacies of the legislation. It’s a 5-minute read that’ll save you hours of time.
Let’s get to it…
What is a Data Protection Officer?
A Data Protection Officer is an expert in data protection law. Their role is to ensure an organisation processes personal data in compliance with the GDPR.
It is a legally required appointment where the processing in question involves regular and systematic monitoring of data subjects on a large scale, or where the processing is of special categories of data on a large scale (the threshold is 5,000 persons).
What is a Subject Access Request?
A Subject Access Request (SAR) is a request for access to personal data. This is the correct legal mechanism under the GDPR for accessing and receiving a copy of personal data as well as other supplementary information held on file.
An individual can make a SAR themselves or have a legal representative do it in writing, verbally, or even on social media. As the ICO says, “a request is valid if it is clear that the individual is asking for their own personal data. An individual does not need to use specific words, refer to legislation or direct the request to a specific contact.”
What is a Data Subject?
A Data Subject is any person with a data file who can be identified directly or indirectly via an identifier from the data collected about them.
Examples of personal identifiers include name and passport number. Identifiers also include physical, physiological, genetic, mental, economic, cultural and social identifiers, such as religion and race.
What is a Data Controller?
A Data Controller is an entity (company, individual, or other body) that controls the means and purpose of processing data. They are the decision-makers with regards to processing. In other words, they instruct the processor.
What is a Data Processor?
A Data Processor is an entity (company, individual, or other body) that processes data on behalf of a Data Controller. They only work on the instructions of the Data Controller. They serve the controller’s interests rather than their own.
What is Profiling?
In the GDPR, Profiling is defined as “any form of automated processing of personal data consisting of the use of personal data to evaluate certain personal aspects relating to a natural person.” Organisations use profiling to predict behaviour, discover user preferences, and make decisions (such as credit decisions).
What is Pseudonymisation?
Pseudonymisation is a data entry technique that replaces or removes certain identifiers from data sets with pseudonyms or values that cannot identify the individual. Controllers will often pseudonymise data so they can use the data beyond the purpose for which it was originally collected. This is allowed under Article 6(4)(e) of the GDPR.
The UK GDPR defines Pseudonymisation as “the processing of personal data in such a way that the data can no longer be attributed to a specific data subject without the use of additional information.”
What is the Data Protection Act?
The Data Protection Act 2018 is UK legislation that sets out the framework for the UK GDPR, a modified version of the EU GDPR with derogations and other provisions.
Put simply, the Data Protection Act 2018 is the UK’s implementation of the EU’s General Data Protection Regulation, which is why you will see the phrase “UK GDPR” used a lot in reference to legislation that applies in the United Kingdom.
Find out more
Our NCSC-certified GDPR training courses are the perfect way for everyone in your organisation to learn more about the GDPR. We can help you get to grips with the GDPR and ensure compliance across your organisation.