Phishing emails remain one of the biggest threats facing both individuals and organisations online. According to analysis from Verizon, 90% of all cyber security incidents and breaches in 2017 included a phishing element, and 76% of organisations experienced a phishing attack.
Of course, not all phishing emails are created equal, ranging from broad attacks around phoney billionaires with trapped funds to specific, targeted campaigns which utilise your publicly available information.
At Bob’s Business, we’re at the forefront of the fight against phishing emails. Our award-winning Think Before you Click phishing simulation finds the vulnerabilities in your organisation and launches targeted training to reduce the likelihood of your workforce clicking on malicious links.
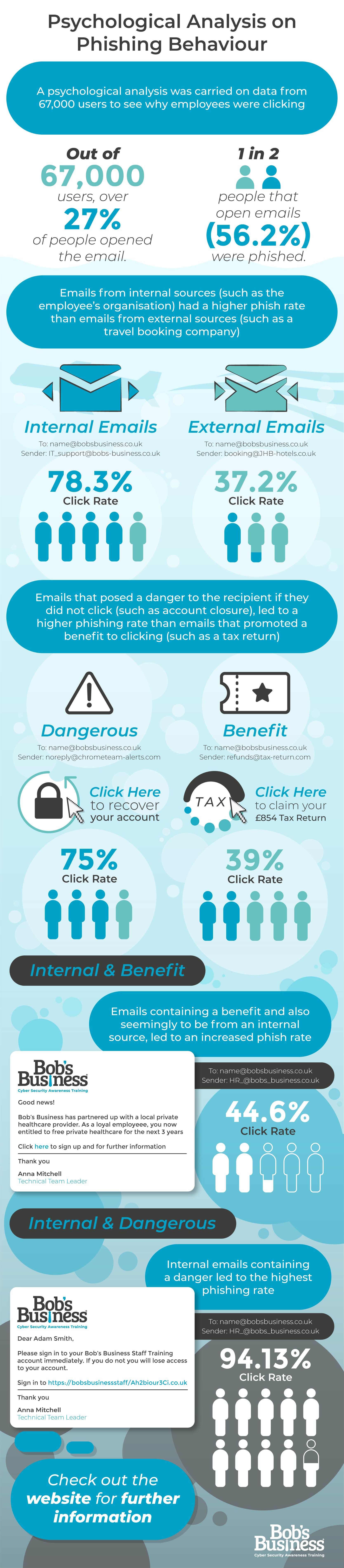
Our approach is deeply rooted in science, which is why, working in conjunction with the University of Huddersfield, we have created a statistical analysis of the results from over 67,000 phishing emails.
The results were stunning and revealed the factors that can lead to a phishing success rate of 94%. But what are those factors, and what can you do to reduce your organisation’s risk of falling victim to an attack? Join us as we share our findings.
What Makes an Effective Phishing Email?
Element #1: Internal vs. External emails
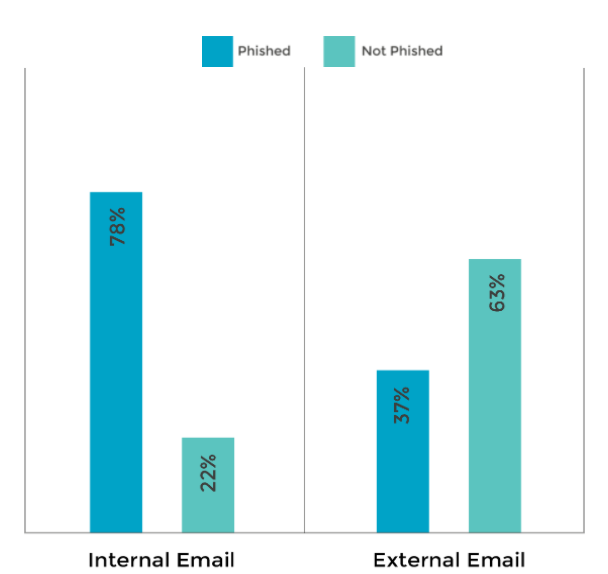
The key factor that determined if a phishing email was a success or not was whether it appeared to come from within the organisation (internal, e.g. an apparent IT security update) or outside the organisation (external, e.g. a discount offer from an online retailer).
Over one in three employees (37.2%) were phished when opening external emails. However, the phishing rate rose to 78% when the emails seemed to be from an internal source. This suggests that employees trust emails that appear to come from internal sources almost twice as much as those from an external source.
Element #2: Danger vs. Benefit
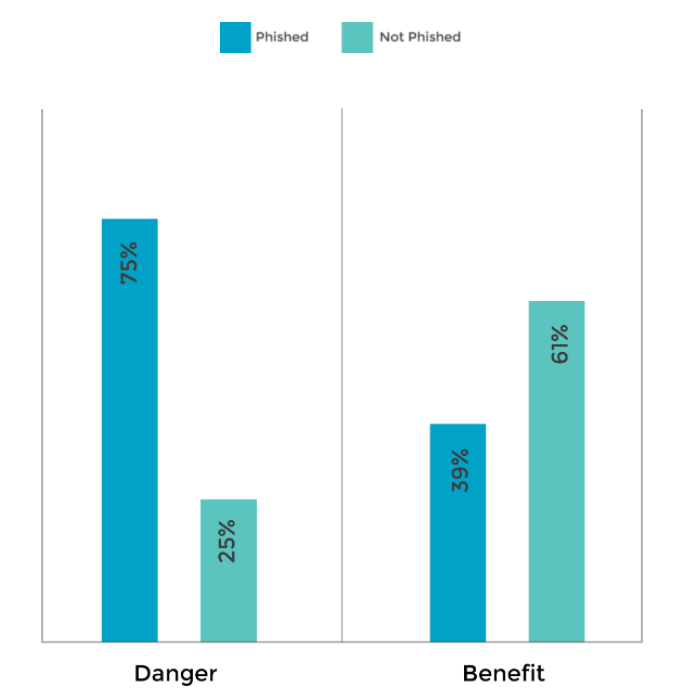
The other factor that determined whether a phishing email was a success or not was whether it employed a ‘danger’ or ‘benefit’ to encourage the recipient to engage with the embedded link.
A ‘danger’ in a phishing email is some sort of risk of loss to the recipient if they do not respond, such as the threat of losing access to an account or a large unexpected bill. A ‘benefit’ might be a voucher for a free product or a tax rebate that requires claiming.
Our research found that a phishing email featuring a ‘danger’ had a phishing success rate of 75%, whilst a phishing email with a ‘benefit’ had a phishing success rate of 39%, clearly indicating that we’re all more likely to act when under pressure.
Combining Factors
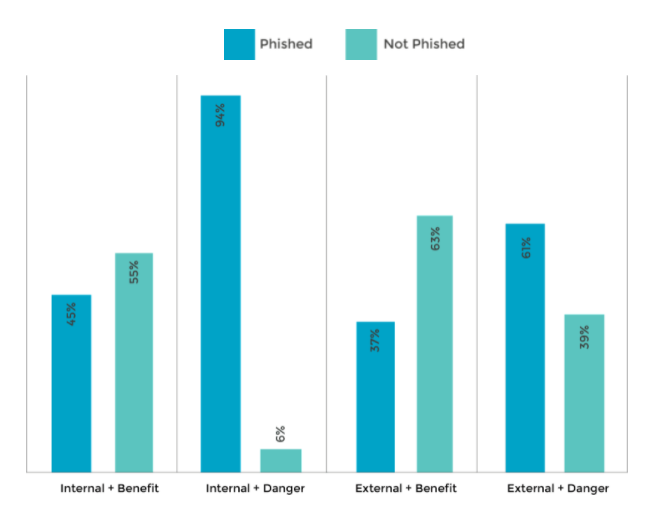
By combining elements, our analysis reveals the common blind spots in organisations.
As expected, phishing emails that posed as internal and included a ‘danger’ were by far the most effective.
The analysis shows that, if the email was from an external source, just over one in three employees (37.2%) clicked on the email and were phished. However, if the email was from an internal source, between 44.6% and 94.1% clicked, depending on whether there was a benefit or a danger that encouraged the user to do so.
If an email was from an internal source and contained a benefit, we saw a phishing rate of just under one in two (44.6%), while internal emails that contained a danger led to a high risk of phishing, with over nine out of ten people being phished (94.13%).
What Can We Learn From This Analysis?
With phishing rates on the rise globally and attacks growing more sophisticated by the day, it’s vital that each of us understands the risks that phishing attacks pose.
Technological solutions offer some protection from phishing attacks, but with analysis of big tech firms finding that only 36% of phishing emails with links were stopped by their systems, it’s clear that more needs to be done to tackle the issue.
It’s especially pressing when you consider that just one phishing email needs to be successful in order to potentially breach your systems.
As such, the only viable option for organisations is to train their staff to better understand how to identify and report phishing emails effectively. By combining a simulated phishing campaign with targeted training, we have found that phishing risk can be reduced by 74.83%.
We firmly believe that focusing on human behaviour and understanding why your employees’ click is the key to reducing risks as training can then be targeted towards changing behaviour.
Book a web demonstration today to learn more about how we can help transform cultures within your organisation.
Download the Infographic
Want to raise awareness of phishing within your organisation, or simply looking for a visual way to share our findings? Click on the infographic below to download your own sharable copy.
Methodology
Bob’s Business’ analysis includes 67,000 users and found that more than 18,000 (26.8%) individuals opened phishing emails. Of these 18,000 that were opened, over 10,000 (56.2%) were successfully phished. All statistics are pulled from the 18,000 individuals who opened the phishing emails.
Contact Us for Comment
Want to discuss our findings? Get in touch with our team at marketing@bobsbusiness.co.uk