Recent years have seen the conversation about cybersecurity move from the IT department to the board room. Cybersecurity is now a top priority at every organisational level, with the number of attacks and potential penalties, both regulatory and in terms of loss of customer trust, increasing.
The potential surface area for an attack has grown rapidly thanks to the complications and costs driven by the Covid-19 pandemic-related shift to a culture of home and remote working that has persisted in many organisations as well as the internet of things (IoT) spreading into every sector of business and society.
Cybersecurity never stands still, however, and with 2023 on the horizon, we thought it valuable to look ahead and predict some of the major trends we foresee playing a role in the next 12 months. Let’s get started:
Recent years have seen the conversation about cybersecurity move from the IT department to the board room. Cybersecurity is now a top priority at every organisational level, with the number of attacks and potential penalties, both regulatory and in terms of loss of customer trust, increasing.
The potential surface area for an attack has grown rapidly thanks to the complications and costs driven by the Covid-19 pandemic-related shift to a culture of home and remote working that has persisted in many organisations as well as the internet of things (IoT) spreading into every sector of business and society.
Cybersecurity never stands still, however, and with 2023 on the horizon, we thought it valuable to look ahead and predict some of the major trends we foresee playing a role in the next 12 months. Let’s get started:
The 5 trends every CISO needs to look out for in 2023
Artificial intelligence (AI) will play an increasingly prominent role in cybersecurity
We’re all only human, and as such, there’s a limit to what we can see, process and respond to.
Human cybersecurity experts are finding it increasingly difficult to respond to all attempted cyberattacks and predict where the most dangerous attacks will occur next, as they have multiplied rapidly.
As such, artificial intelligence (AI) may prove to be an increasingly valuable tool. Machine learning algorithms can study the massive amounts of data flowing across networks in real-time more efficiently than humans can and learn to spot patterns that indicate a threat.
Unfortunately, hackers and criminals are growing more skilled at exploiting AI as it becomes more readily available. Just as security experts can utilise AI for good, so can criminals.
Bad actors use artificial intelligence algorithms to find vulnerable systems or networks among the millions of computers and networks linked to the internet. The ability to automate the mass production of personalised phishing emails has been another significant use, and such emails are getting better at dodging automatic email defence systems too.
The use of AI in cybersecurity has even been given its own name and is commonly referred to as an ‘arms race’ as hackers and cyber professionals race to ensure the newest and most sophisticated algorithms are working on their side as opposed to against them.
It’s been predicted that by 2030 the market for AI cybersecurity products will be worth close to $139 billion – a ten times increase on the value of the 2021 market.
Building a security-aware culture will be more vital than ever
Developing and fostering a culture of awareness around cybersecurity risks is the most crucial measure that can be made at any organisation. Employers and employees can no longer simply consider cybersecurity to be an issue that the IT department should handle.
In reality, everyone’s work description in 2023 should include developing an awareness of the threats and taking basic precautions to ensure safety!
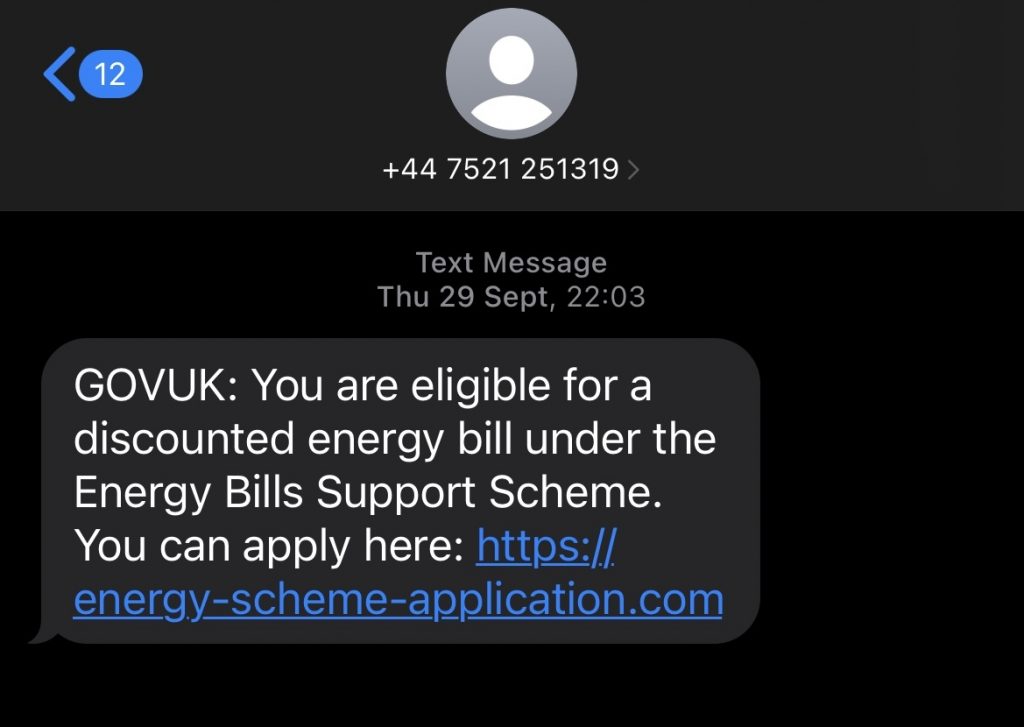
Phishing attacks use social engineering techniques to trick victims into disclosing sensitive information or installing malware on their computers.
Even without technical expertise, anyone can learn to recognise these types of attacks and take simple safety precautions to protect themselves. That’s why implementing cybersecurity awareness training within every organisation, irrespective of size will be fundamental for the success of any organisation in 2023.
Similarly, fundamental security skills such as secure password usage and understanding two-factor authentication (2FA) should be taught to everyone and regularly updated. Taking simple safeguards like these to promote a culture of cybersecurity awareness should be a major component of business strategy if an organisation wants to ensure that they create resilience and preparation over the next 12 months.
Increased accountability will be demanded supply chain
Customers’ inspection of the security supply chain will intensify in 2023. The Cyber Resiliency Act is already in effect in Europe, and a modification to the NIST framework is being proposed in the UK to transfer some accountability to the providers.
Due to the growing risk of fines, rising costs and the complexity of cyber insurance, businesses will under increased pressure from both customers and authorities to offer security solutions that have been accredited. Expect a 9% increase in 2023 in the number of UK companies being penalised for failing to protect sensitive information and personal data.
Curious to discover more about how to defend your organisation against supply chain attacks? Read our blog on supply chain attacks here.
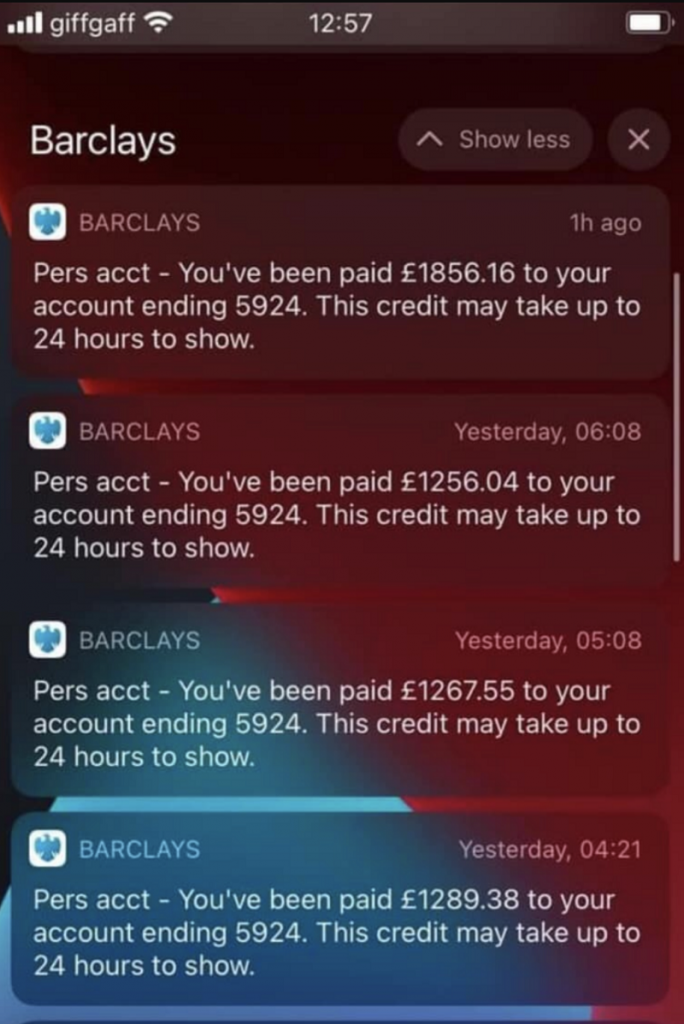
Mobile will be the new target
In 2019, mobile banking malware or attacks are expected to expand significantly, by as much as 50%, making our handheld devices a seriously viable target for hackers.
With personal computing shifting away from the laptop and desktop PC, it’s no surprise to hear that our phones are the new frontier. Keep a close eye out for stories around smartphone security, with malware or viruses specifically designed to affect smartphones in 2023.
IoT on 5G networks will be under the magnifying glass
With the launch and expansion of 5G networks, the Internet of Things will usher in a new era of interconnectivity (IoT). Additionally, because of the connectivity between numerous devices, they are vulnerable to outside interference, attacks, or unidentified software bugs.
Even Chrome, the most popular browser in the world, has been found to contain significant security faults over the years. Because 5G architecture is still relatively new in the market, extensive study is needed to identify vulnerabilities and strengthen the system’s defences against outside attacks. The 5G network may experience several network attacks at every stage that we are unaware of.